The concept of cyber security is outside of the usual digital marketing tips you find on this blog. However, with the Canadian Centre for Cyber Security reporting on over 40 alerts and advisories so far this month a sidebar is justified, if not critical. You see, your social media strategy could be putting you at undue risk. This risk is not just to your social media profiles, but to your entire operations. Below is a breakdown of what you need to do and watch out for.
6 Ways to Reduce the Risk of Social Media Marketing Cyber Crime
I. Limit Admin Access for Your Social Media Managers
Many organizations have more than one staff member post on social media on behalf of the company. It can be an efficient way to keep followers engaged through all hours of the day while building an employee advocacy program for your organization.
The problem is that when too many people have access to your social media profiles it creates risk. You do not need to revoke access, but you do need to limit top-level administrators.
The social media profiles that your company uses offer varying levels of access. For instance, Facebook allows you to set the following Page Roles:
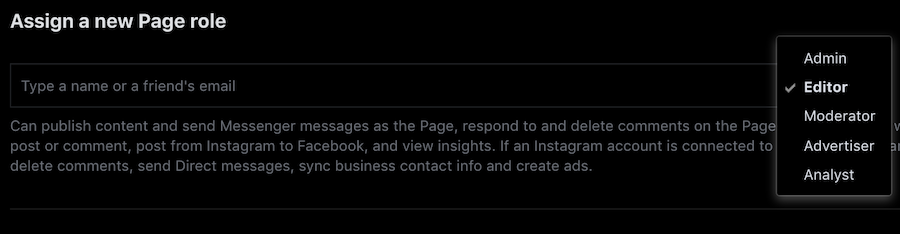
Only top-level marketing staff should have Admin access. Anyone else who needs to post on behalf of your brand should be made an Editor. If you outsource social media advertising from a contractor and need them to be able to create ads, promotions or boosted posts for Facebook, then they will be assigned as an Advertiser. If other personnel are only required to respond to and delete comments and posts to the Page, they should be made a Moderator. (View more on Facebook Page Roles here.)
For Instagram, ensure that your brand profile is designated as a business account, which will allow you to edit Page Roles and add people to your Ad account. View more on Instagram Page Roles here.
For your organization’s other social media profiles, check current Page Roles and ensure that Admin access is limited by referencing the following:
II. MFA for BYOD
Social media applications are designed to be managed by mobile devices. Those (yourself included) who manage social media marketing do so from airports, coffee shops, and a variety of other remote locations. Ideally your organization would provide social media marketing staff with company provided devices and install multi factor authentication (MFA). If devices are lost or stolen, MFA will ensure that social applications cannot be accessed. However, since most commercial operations have adopted a bring-your-own-device (BYOD) culture, you must require that marketing staff have IT install MFA on their personal devices.
III. Make Staff Aware of C-Level Phishing on Social
C-level spear phishing is when a cyber criminal impersonates a CEO, CFO, CMO or other executives (via digital communication) to trick subordinates in order to gain access to sensitive data.
Under an employee advocacy program executives and staff alike communicate regularly via social media, especially when in reference to marketing campaigns that occur on the same platforms. This is fine, if it is understood that there should never be a request for access, passwords, documents, or any form of sensitive information over messaging applications. This is because cybercriminals create close-matching social media profiles to impersonate C-level executives. They then connect to company subordinates, and when the time is right, they casually make their request. Someone serving in a subordinate capacity is unlikely to question the authenticity of a request when they think it is coming from a superior, which is why this criminal strategy has proven effective.
To keep this from happening, establish a clear protocol that no one (including top level executives) shall ever request access, passwords, documents, and data via Facebook/Instagram Messenger or any other social media communications tool. Only traditional (and secure) forms of corporate communication channels should be used for this sort of thing.
IV. Click No “Customer” Links or Attachments in Messenger
Recent data has shown that approximately 50% of consumers use social media as a form of product/service support; to make product/service queries or complaints. It is ill-advised to dictate to the consumer that such communications would be preferred over email or the phone, you may need to manage their requests on the social platform to protect yourself from cybercrime. For example, ensure that staff does not click on a link or attachment that has been added (by the perceived customer) to a conversation on social. A cybercriminal disguising themselves as a customer will hide a malicious program in a link that is purported to be a photo or video of a defective product, etc. If they insist on sending a link/attachment, you can require that they send it over via email, to which you have appropriate cybersecurity software installed.
V. Watch Your Background
Consumer engagement can increase when brands open the doors to their offices and give them a peak into corporate culture via their social networks. It is a social media marketing strategy that fosters trust and subsequently sales. We absolutely encourage the act of showcasing your company environment on social media. However, take practical steps to protect yourself from the prying eyes of cybercriminals who will screenshot and freeze-frame video and carefully inspect photos of your commercial spaces to see if there is anything they can use against you. Make sure that when shooting content that there are no visible whiteboards, computer screens or anything else that gives up sensitive information.
VI. Let Pros Manage Your Social Media Marketing Instead
Social media marketing is already a fulltime job. If you add cyber security concerns to the mix you and/or staff will spend countless of hours questioning and rethinking every social post and communication. To avoid being bogged down and losing focus on the rest of your business, engage the services of a social media marketing specialist. Contact Strategis Consulting Group today to schedule a consultation.

